I’m trying to set up an Azure point-to-site VPN connection, and I’m receiving the following error: “ The remote access connection completed, but authentication failed because the certificate that authenticates the client to the server is not valid. Ensure that the certificate used for authentication is valid.
Simplest solution for OS X Point-to-Site VPN access to an Azure VNet. Because the IP addresses of the VPN clients are not registered in Azure and are un-routable. Every VPN client should use the VPN server's internal IP address as the source address when it tries to access the resource in VNET. Are you (Microsoft) going to provide a VPN Client for MAC OSx? The VPN client for Windows is great and works well. However I have a genuine need to enable users on MAC's to connect via VPN to Azure to run VM's etc, and hence it would be great to have these users able to utilize the Azure VM's.
We've been using Azure's built-in VNet/VPN solution, with a combination of both point-to-site and site-to-site connections, and so far it's worked reasonably well. But our company is very - very - distributed, and we need to grant some remote OS X clients access to resources inside our Azure VNet. And of course, despite it being one of the top requests on UserVoice, MS doesn't support any non-Windows client in their Point-to-Site VPN configuration.
Aug 14, 2013 Hi there. Are you (Microsoft) going to provide a VPN Client for MAC OSx? The VPN client for Windows is great and works well. However I have a genuine need to enable users on MAC's to connect via VPN to Azure to run VM's etc, and hence it would be great to have these users able to utilize the Azure VM's. I am trying to connect my Macbook to an Azure VPN. Each time I try to connect the connection animation of the VPN icon on the top bar goes on for a few seconds and then stops, without any explanations about what went wrong.I followed all the instructions to the letter, double, triple and quadruple-checked everything. In order to initiate a VPN session, you need to download and install a VPN package on your client machine. Depending upon whether your client machine is a 32 bit machine or 64 bit, pick the appropriate download link from the page shown above.
So I'm left looking for other options. One possibility, of course, would be to configure each of the remote home offices with, say, a Dell Sonicwall, and configure that Sonicwall with a Site-to-Site VPN connection. But that gets expensive and complicated, and still doesn't allow them to, say, connect to the VPN if they're on the road or at a coffee shop.
So I've been looking into some of the VPN solutions that show up on the Azure marketplace - for instance, VNS3 from Cohesive, or SohaCloud, or pfSense, or whatever. The problem is that these all seem to be focused on the (much more complex) Site-to-Site configuration style - at least, that's what all their documentation seems to be pointing to (for instance, https://cohesive.net/dnld/Cohesive-Networks_VNS3-3.5-Azure.pdf). And all I want is a really simple Point-to-Site configuration.
What's my best (meaning simplest) option here? I'm no network guy, and I start feeling out of my depth (and like I'm headed down a rathole) whenever I start trying to translate the documentation into my particular scenario.
I certainly can't be the only person who's had to figure out how to let OS X clients into an Azure VNet - what's the recommended approach here?
2 Answers
They now support the mac natively using IKEv2: https://docs.microsoft.com/en-us/azure/vpn-gateway/point-to-site-vpn-client-configuration-azure-cert#installmac
You have two workarounds:
- Install a Windows Server on the Azure and connect it to the VNET. You may use it as a jumpbox to access the resource on the VNET.
Note: Windows Server only allow 2 users login at same time. If you need to let more than 2 users to connect to the jumpbox, you need to install the RDS services and purchase the CAL.
- Install a VPN server on Azure and let your clients connect to the VPN server.
Note: You need to enable the NAT on the VPN server, because the IP addresses of the VPN clients are not registered in Azure and are un-routable. Every VPN client should use the VPN server's internal IP address as the source address when it tries to access the resource in VNET.
Not the answer you're looking for? Browse other questions tagged vpnmac-osxazure or ask your own question.
| title | description | services | author | ms.service | ms.topic | ms.date | ms.author |
|---|---|---|---|---|---|---|---|
Connect a computer to an Azure virtual network using Point-to-Site and native Azure certificate authentication: Azure Portal Microsoft Docs | Connect Windows, Mac OS X, and Linux clients securely to an Azure virtual network using P2S and self-signed or CA issued certificates. This article uses the Azure portal. | cherylmc | conceptual | cherylmc |
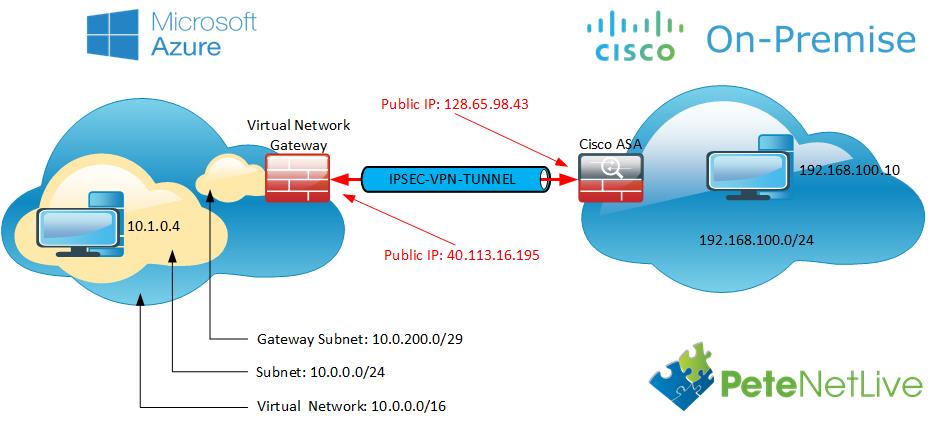
This article helps you securely connect individual clients running Windows, Linux, or Mac OS X to an Azure VNet. Point-to-Site VPN connections are useful when you want to connect to your VNet from a remote location, such when you are telecommuting from home or a conference. You can also use P2S instead of a Site-to-Site VPN when you have only a few clients that need to connect to a VNet. Point-to-Site connections do not require a VPN device or a public-facing IP address. P2S creates the VPN connection over either SSTP (Secure Socket Tunneling Protocol), or IKEv2. For more information about Point-to-Site VPN, see About Point-to-Site VPN.
Architecture
Point-to-Site native Azure certificate authentication connections use the following items, which you configure in this exercise:
- A RouteBased VPN gateway.
- The public key (.cer file) for a root certificate, which is uploaded to Azure. Once the certificate is uploaded, it is considered a trusted certificate and is used for authentication.
- A client certificate that is generated from the root certificate. The client certificate installed on each client computer that will connect to the VNet. This certificate is used for client authentication.
- A VPN client configuration. The VPN client configuration files contain the necessary information for the client to connect to the VNet. The files configure the existing VPN client that is native to the operating system. Each client that connects must be configured using the settings in the configuration files.
Example values
You can use the following values to create a test environment, or refer to these values to better understand the examples in this article:
- VNet Name: VNet1
- Address space: 192.168.0.0/16
For this example, we use only one address space. You can have more than one address space for your VNet. - Subnet name: FrontEnd
- Subnet address range: 192.168.1.0/24
- Subscription: If you have more than one subscription, verify that you are using the correct one.
- Resource Group: TestRG
- Location: East US
- GatewaySubnet: 192.168.200.0/24
- DNS Server: (optional) IP address of the DNS server that you want to use for name resolution.
- Virtual network gateway name: VNet1GW
- Gateway type: VPN
- VPN type: Route-based
- Public IP address name: VNet1GWpip
- Connection type: Point-to-site
- Client address pool: 172.16.201.0/24
VPN clients that connect to the VNet using this Point-to-Site connection receive an IP address from the client address pool.
1. Create a virtual network
Mac Vpn Setup
Before beginning, verify that you have an Azure subscription. If you don't already have an Azure subscription, you can activate your MSDN subscriber benefits or sign up for a free account.[!INCLUDE Basic Point-to-Site VNet]
2. Add a gateway subnet
Before connecting your virtual network to a gateway, you first need to create the gateway subnet for the virtual network to which you want to connect. The gateway services use the IP addresses specified in the gateway subnet. If possible, create a gateway subnet using a CIDR block of /28 or /27 to provide enough IP addresses to accommodate additional future configuration requirements.
[!INCLUDE vpn-gateway-add-gwsubnet-rm-portal]
3. Specify a DNS server (optional)
After you create your virtual network, you can add the IP address of a DNS server to handle name resolution. The DNS server is optional for this configuration, but required if you want name resolution. Specifying a value does not create a new DNS server. The DNS server IP address that you specify should be a DNS server that can resolve the names for the resources you are connecting to. For this example, we used a private IP address, but it is likely that this is not the IP address of your DNS server. Be sure to use your own values. The value you specify is used by the resources that you deploy to the VNet, not by the P2S connection or the VPN client.
[!INCLUDE vpn-gateway-add-dns-rm-portal]
4. Create a virtual network gateway
[!INCLUDE create-gateway]
[!NOTE]The Basic gateway SKU does not support IKEv2 or RADIUS authentication. If you plan on having Mac clients connect to your virtual network, do not use the Basic SKU.
5. Generate certificates
Certificates are used by Azure to authenticate clients connecting to a VNet over a Point-to-Site VPN connection. Once you obtain a root certificate, you upload the public key information to Azure. The root certificate is then considered 'trusted' by Azure for connection over P2S to the virtual network. You also generate client certificates from the trusted root certificate, and then install them on each client computer. The client certificate is used to authenticate the client when it initiates a connection to the VNet.
1. Obtain the .cer file for the root certificate
[!INCLUDE root-certificate]
2. Generate a client certificate
[!INCLUDE generate-client-cert]
6. Add the client address pool
The client address pool is a range of private IP addresses that you specify. The clients that connect over a Point-to-Site VPN dynamically receive an IP address from this range. Use a private IP address range that does not overlap with the on-premises location that you connect from, or the VNet that you want to connect to.
Once the virtual network gateway has been created, navigate to the Settings section of the virtual network gateway page. In the Settings section, click Point-to-site configuration.
Click Configure now to open the configuration page.
On the Point-to-site configuration page, in the Address pool box, add the private IP address range that you want to use. VPN clients dynamically receive an IP address from the range that you specify. The minimum subnet mask is 29 bit for active/passive and 28 bit for active/active configuration. Click Save to validate and save the setting.
[!NOTE]If you don't see Tunnel type or Authentication type in the portal on this page, your gateway is using the Basic SKU. The Basic SKU does not support IKEv2 or RADIUS authentication.
7. Configure tunnel type
You can select the tunnel type. The tunnel options are OpenVPN, SSTP and IKEv2. The strongSwan client on Android and Linux and the native IKEv2 VPN client on iOS and OSX will use only IKEv2 tunnel to connect. Windows clients try IKEv2 first and if that doesn’t connect, they fall back to SSTP. You can use the OpenVPN client to connect to the OpenVPN tunnel type.
8. Configure authentication type
Select Azure certificate.
9. Upload the root certificate public certificate data
You can upload additional trusted root certificates up to a total of 20. Once the public certificate data is uploaded, Azure can use it to authenticate clients that have installed a client certificate generated from the trusted root certificate. Upload the public key information for the root certificate to Azure.
Certificates are added on the Point-to-site configuration page in the Root certificate section.
Make sure that you exported the root certificate as a Base-64 encoded X.509 (.cer) file. You need to export the certificate in this format so you can open the certificate with text editor.
Open the certificate with a text editor, such as Notepad. When copying the certificate data, make sure that you copy the text as one continuous line without carriage returns or line feeds. You may need to modify your view in the text editor to 'Show Symbol/Show all characters' to see the carriage returns and line feeds. Copy only the following section as one continuous line:
Paste the certificate data into the Public Certificate Data field. Name the certificate, and then click Save. You can add up to 20 trusted root certificates.
Click Save at the top of the page to save all of the configuration settings.
10. Install an exported client certificate
If you want to create a P2S connection from a client computer other than the one you used to generate the client certificates, you need to install a client certificate. When installing a client certificate, you need the password that was created when the client certificate was exported.
Make sure the client certificate was exported as a .pfx along with the entire certificate chain (which is the default). Otherwise, the root certificate information isn't present on the client computer and the client won't be able to authenticate properly.
For install steps, see Install a client certificate.
11. Generate and install the VPN client configuration package
The VPN client configuration files contain settings to configure devices to connect to a VNet over a P2S connection. For instructions to generate and install VPN client configuration files, see Create and install VPN client configuration files for native Azure certificate authentication P2S configurations.
12. Connect to Azure
To connect from a Windows VPN client
[!NOTE]You must have Administrator rights on the Windows client computer from which you are connecting.
To connect to your VNet, on the client computer, navigate to VPN connections and locate the VPN connection that you created. It is named the same name as your virtual network. Click Connect. A pop-up message may appear that refers to using the certificate. Click Continue to use elevated privileges.
On the Connection status page, click Connect to start the connection. If you see a Select Certificate screen, verify that the client certificate showing is the one that you want to use to connect. If it is not, use the drop-down arrow to select the correct certificate, and then click OK.
Your connection is established.
Troubleshoot Windows P2S connections
[!INCLUDE verifies client certificates]
To connect from a Mac VPN client
From the Network dialog box, locate the client profile that you want to use, specify the settings from the VpnSettings.xml, and then click Connect.
Check Install - Mac (OS X) for detailed instructions. If you are having trouble connecting, verify that the virtual network gateway is not using a Basic SKU. Basic SKU is not supported for Mac clients.
To verify your connection
These instructions apply to Windows clients.
To verify that your VPN connection is active, open an elevated command prompt, and run ipconfig/all.
View the results. Notice that the IP address you received is one of the addresses within the Point-to-Site VPN Client Address Pool that you specified in your configuration. The results are similar to this example:
To connect to a virtual machine
These instructions apply to Windows clients.
[!INCLUDE Connect to a VM]
To add or remove trusted root certificates
You can add and remove trusted root certificates from Azure. When you remove a root certificate, clients that have a certificate generated from that root won't be able to authenticate, and thus will not be able to connect. If you want a client to authenticate and connect, you need to install a new client certificate generated from a root certificate that is trusted (uploaded) to Azure.
To add a trusted root certificate
You can add up to 20 trusted root certificate .cer files to Azure. For instructions, see the section Upload a trusted root certificate in this article.
To remove a trusted root certificate
- To remove a trusted root certificate, navigate to the Point-to-site configuration page for your virtual network gateway.
- In the Root certificate section of the page, locate the certificate that you want to remove.
- Click the ellipsis next to the certificate, and then click 'Remove'.
To revoke a client certificate
You can revoke client certificates. The certificate revocation list allows you to selectively deny Point-to-Site connectivity based on individual client certificates. This is different than removing a trusted root certificate. If you remove a trusted root certificate .cer from Azure, it revokes the access for all client certificates generated/signed by the revoked root certificate. Revoking a client certificate, rather than the root certificate, allows the other certificates that were generated from the root certificate to continue to be used for authentication.
The common practice is to use the root certificate to manage access at team or organization levels, while using revoked client certificates for fine-grained access control on individual users.
Revoke a client certificate
You can revoke a client certificate by adding the thumbprint to the revocation list.
- Retrieve the client certificate thumbprint. For more information, see How to retrieve the Thumbprint of a Certificate.
- Copy the information to a text editor and remove all spaces so that it is a continuous string.
- Navigate to the virtual network gateway Point-to-site-configuration page. This is the same page that you used to upload a trusted root certificate.
- In the Revoked certificates section, input a friendly name for the certificate (it doesn't have to be the certificate CN).
- Copy and paste the thumbprint string to the Thumbprint field.
- The thumbprint validates and is automatically added to the revocation list. A message appears on the screen that the list is updating.
- After updating has completed, the certificate can no longer be used to connect. Clients that try to connect using this certificate receive a message saying that the certificate is no longer valid.
Point-to-Site FAQ
Azure Vpn Client For Mac
[!INCLUDE Point-to-Site FAQ]
Azure Virtual Vpn
Next steps
Once your connection is complete, you can add virtual machines to your virtual networks. For more information, see Virtual Machines. To understand more about networking and virtual machines, see Azure and Linux VM network overview.
For P2S troubleshooting information, Troubleshooting Azure point-to-site connections.